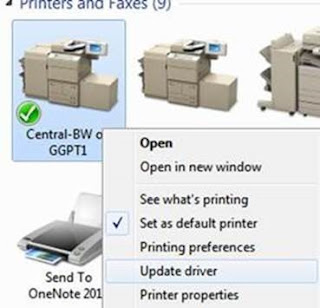
Issues Updating Print Drivers | KB3170455
Recently a client of mine updated their print drivers on the Print Server (through Print Managemnet). Users suddenly had issues printing, where Word would say “Driver Update Required“. When a user would go to right-click on the printer and click on “Update Driver“, they would get essentially a UAC prompt asking whether they trust that particular printer:
When they click Install Driver, it looks like it’s installing and then it just falls back to the same message. It looks like there’s an endless loop where users can’t print because of the driver update requirement, but they can’t install the driver either.
These printers are deployed through Print Management and are deployed via GPO. There are Point and Print restriction policies in place as well to remove any warnings or UAC prompts for installing new drivers, or updating drivers:
- Package aware
- Digitally signed
- Catalogue print drivers
There’s currently only two options to get around this:
- Download another driver that meets the criteria
- Remove the Windows Security Update from all servers and workstations
Intel SCS Task Sequences not working with SCCM 2012 R2 | Intel AMT: Configuration
This post follows on from my previous post which was about running a Task Sequence for Intel AMT: Discovery. This post is in relation to the next Task Sequence in the list, which is called Intel AMT: Configuration.
This Task Sequence has the following details within SCCM:
Essentially the %% details are taken from within the Configure.bat script. Running the TS isn’t a problem, but it is deciding to fail when after it’s downloaded the required data:
So we’ve got a few errors here. TCP Error, Caller is unauthorised, Valid password not found. From here I checked the SMSTS.log files to see what was happening. The logs were about 41 pages long, so I’m not going to copy it all here, but there were various errors within this:
<![LOG[Failed to run the action: Intel AMT: Configuration.
The process cannot access the file because another process has locked a portion of the file. (Error: 00000021; Source: Windows)]LOG]!><time=”15:10:04.029-480″ date=”07-14-2016″ component=”TSManager” context=”” type=”3″ thread=”2724″ file=”instruction.cxx:895″>
I had a look at the Configuration.bat file that the Task Sequence was calling and made a few changes to the contents:
I also ensured that the following contents had been edited so it was showing the correct SCCM server, and site:
Once I had done this, I ran the batch file again from the local workstation (instead of running it through Software Center) so I could see how it was running, and whether there were any error messages etc. This time it progressed a lot further than before. I don’t have a screenshot of the error message that I was getting this time, but it was essentially connecting to the AMT device and then erroring out saying that the password was incorrect.
Looking into the setup of the whole script/software, it looks like Intel SCS and Intel AMT: Configure relies on AMT not being configured on the local device. What had happened was this device had been setup with MEBx (which is essentially the AMT login through BIOS) where it forces you to reset the password. When this script was trying to connect to the device, it was using the default “admin” password which was incorrect as it had been changed. This is why it was failing.
The only way to get around this was to take out the CMOS battery to completely reset the BIOS and MEBx. After doing this, I confirmed that the “admin” password was back in, not the custom password we had originally configured. When running the script now through Software Center, it works!!
After doing this, I was able to Discover AMT Status through SCCM:
Once that was complete, it now showed me that the device had been externally provisioned!
We can now control the device through SCCM:
Intel SCS Task Sequences not working with SCCM 2012 R2 | Intel AMT: Discovery
Recently I have been labbing a new setup with SCCM 2012 R2 with Intel SCS. The idea was to get Out of Band Management working with SCCM for some workstations which had Intel AMT. I followed this guide, which was very helpful in getting everything setup. The only difference was that I was using the latest version of Intel SCS 11.0 rather than version 9.0. When I ran into some issues (and let’s face it, you always run into issues when using SCCM), I noticed that there was literally nothing online with regard to the issue I was having…so here it is!
The problem I hit was when I was enabling the various Task Sequences to run discovery and configuration of the workstations for Intel AMT. The first task sequence works fine, which is Intel SCS Platform Discovery. The second task sequence however; Intel AMT Discovery fails when I try to run it. I’m not really able to find out what is going on through the logs, as you know with SCCM, it’s almost impossible to find anything as there’s like 1,000,000 logs to sift through.
Looking into the Task Sequence, all it does it call up a batch file called Discover.bat. I ran this script manually, adding a pause command at the end so I could see what was going on. I noticed the following errors:
So it looks like there’s nothing wrong with SCCM, and there’s potentially nothing wrong with the batch script. The issue looks to be certificate related. Great!
Looking at the batch file, it calls an Executable file to run. I opened this file up (right-click, Properties), then checked the Digital Signatures of the file:
As you can see, there’s a lot of intermediary certificates that are required. I only had the Root CA certificate installed. I went through that list and installed each certificate, then ran the Task Sequence again from Software Center (through SCCM). This time it was successful. In future, we will need to ensure that these certificates are exported and then deployed to all computers within the network.
WSUS Fails to Connect
Recently I had a WSUS server which had to be rebooted. Upon restarting the server, I noticed that I could no longer get into the WSUS console. When trying to connect I was receiving the following error message:
Checking the Event Logs, I found two events which showed the following:
My next step was to check the health of WSUS with the following command:
WsusUtil.exe checkhealth
This was run from “C:\Program Files\Update Services\Tools” directory
Running this command gave me the following result:
Upon looking into this further, I noticed that there was a Windows Update which has caused some issues in the past for some people. The update is KB3159706. I checked my server and I did not have this update installed, but thought I would humour it and try the fix anyway. The fix mentioned in the KB article actually resolved the issue. I did the following to get it back up and running:
1. Install the HTTP Activation role under .NET Framework 4.5 Features through Server Manager.
Remote Desktop licensing mode is not configured
Recently when I was on a client’s server, I noticed a message popping up saying that Remote Desktop licensing mode was not configured.
When looking at the RD Licensing Diagnoser, it showed the following details:
The warning says “The licensing mode for the Remote Desktop Session HOst server is not configured“. Down the bottom of the screen, you can also see “The Remote Desktop Session Host server is not configured with any license server“.
To fix this problem you will need to run two PowerShell commands to ensure that the server is targeting the correct licensing server. The commands are the following:
$obj = gwmi -namespace “Root/CIMV2/TerminalServices” Win32_TerminalServiceSetting
$obj. SetSpecifiedLicenseServerList(“licserver.domain.local”)
Change the last section to ensure that the FQDN of the licensing server has been added in. Once you’ve done that final command, you should see the following:
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM\Licensing Core\LicensingMode
LicensingMode is a DWORD which will need to have it’s value changed. Your options are below:
2 – Per Device
4 – Per User
I changed mine to ‘4’ as I wanted it to be licensed ‘per user’.
File Server Resource Manager (FSRM) showing inaccurate quota usage
Recently a client of mine came to me saying that File Server Resource Manager (FSRM) Quotas wasn’t reporting accurately. On this particular network, Folder Redirection had been enabled and all data was being redirected back to the file server. There was a 250MB quota setup for each user’s redirected folder (ie Desktops has 250MB limit).
FSRM Quotas was showing that a particular user’s Desktop folder was using 160% of the quota limit.
When checking how much data is actually being used in that folder through FSRM, it shows the following:
When checking the file location, it’s also showing that the folder is empty. I ensured that Hidden Folders were being shown.
Checking the ‘Size on Disk’, it definitely gave the same file size of 401mb, so I knew that there’s definitely something within that folder that’s not being shown to me. I checked the view settings of the folder and had to un-tick the following item:
So now we have worked out why FSRM is showing what it’s showing, we need to remove all the Recycle Bin files from each user’s Folder Redirection location. This was relatively easy, and I did it with a batch script, which had the following in it:
for /d %%i in (E:\Users\FolderRedirection\Desktops\*) do @ rd /q/s “%%i\$Recycle.Bin
for /d %%i in (E:\Users\FolderRedirection\Documents\*) do @ rd /q/s “%%i\$Recycle.Bin
for /d %%i in (E:\Users\FolderRedirection\Pictures\*) do @ rd /q/s “%%i\$Recycle.Bin
for /d %%i in (E:\Users\FolderRedirection\Music\*) do @ rd /q/s “%%i\$Recycle.Bin
for /d %%i in (E:\Users\FolderRedirection\Videos\*) do @ rd /q/s “%%i\$Recycle.Bin
pause
Running this script goes through all the usernames and then removes all the $Recycle.Bin files within the specific folders. You will need to adjust the location to ensure that it’s targeting the correct folders within your network.